 With perfect password manager, I thought I had the complete set of tools in my Mac for getting things done. But today I realized, I’d overlooked ethereal. I use it sometimes and it’s a gem without which it would be very difficult to solve some network problems. Ethereal is a free and open source packet sniffer application, used for network troubleshooting, analysis, software and protocol development, and education. It has all of the standard features of a protocol analyzer.
With perfect password manager, I thought I had the complete set of tools in my Mac for getting things done. But today I realized, I’d overlooked ethereal. I use it sometimes and it’s a gem without which it would be very difficult to solve some network problems. Ethereal is a free and open source packet sniffer application, used for network troubleshooting, analysis, software and protocol development, and education. It has all of the standard features of a protocol analyzer.
I was happy to see Ethereal for Mac OS X listed at the top of the download page. But, was confused with the choice I had to make between Fink Project and DarwinPorts. I was not sure what they meant or which one was better. So, after Googling a while and reading the FAQs, I found that the number one goal of both projects were to port open source Linux/Unix softwares to Mac OS X. They just differ in the packaging approach they’ve taken. DarwinPorts was written from scratch to try a different approach to a packaging system, where as Fink Project utilizes robust package management tools dpkg and apt-get from Debian Linux Project . So, I decided to try ethereal with Fink Project and this is how I did it.
Read more ›
 This Multifunctional Broadrange Wireless Router from AUSUS is amazing. It’s a perfect one box solution for your Home Wireless Network, Internet Connection and Digital Media Storage. All this in a small box:
This Multifunctional Broadrange Wireless Router from AUSUS is amazing. It’s a perfect one box solution for your Home Wireless Network, Internet Connection and Digital Media Storage. All this in a small box: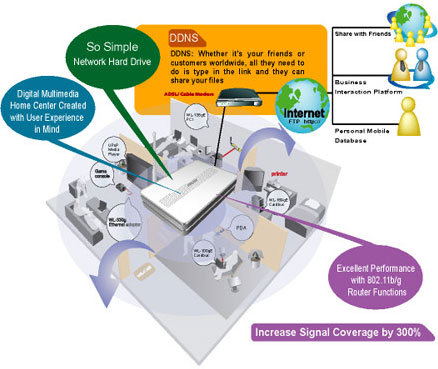
 Firewalls have become an integral part of all corporate networks. They’re the first line of defense against attacks from outside network (Internet) and also the point of control to make sure internal users (employees) are using the Internet as they’re supposed to. Recently the
Firewalls have become an integral part of all corporate networks. They’re the first line of defense against attacks from outside network (Internet) and also the point of control to make sure internal users (employees) are using the Internet as they’re supposed to. Recently the 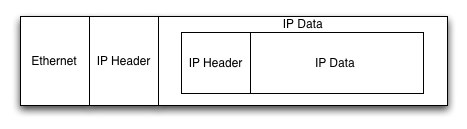

 With
With  After
After
Recent Comments