Secure, Easy and Cheap VPN: OpenVPN
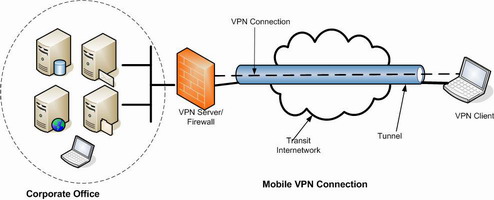
I’ve used IPSec, PPTP and SSL VPNs for quite some time and found them to have their own strengths and weaknesses. IPSec is secure but too complicated, with too many options for implementation and configuration. PPTP is easy to use and configure but it had some security issues in the past, which deters serious security minded organizations to implement it. Commercial SSL VPNs are easy to use but they’re very expensive and still haven’t solved all the remote connection problems.
I was introduced to SoftEther (popular Japanese personal VPN) by one of my boss few years ago, it’s secure and free but the documents are available only in Japanese. While I was searching for english documents of SoftEther, I came across an Wikipedia entry, which said “It is similar to OpenVPN, though it is closed source software”. I’d heard about OpenVPN but had never given it a serious look. This time I decided to look at it. I was pleasantly surprised by it’s ease of installation, use and robust security. Here are few points to note about OpenVPN:
- It’s a free and opensource.
- It’s secure; uses the SSL/TSL protocol.
- It’s easy to install and use. Graphical User Interfaces are available for those who fear the command lines.
- Has flexible authentication scheme based on certificates, smart cards, or traditional username/password credentials.
- Can be implemented as a bridge or a router (OSI layer 2 or layer 3).
- Excellent cross-platform support, it can be installed in Linux, Unix, Windows and Mac OS X.
- Good documentation, FAQs, HowTos and articles.
If you’re looking for a secure, cheap, flexible and easy to use vpn solution, then you should give OpenVPN a try.

 Most of the modern Ethernet networks use LAN switches and for the Network Admins it’s very essential to understand how this basic, yet very important component of the network operates. I came across an excellent document in cisco site about
Most of the modern Ethernet networks use LAN switches and for the Network Admins it’s very essential to understand how this basic, yet very important component of the network operates. I came across an excellent document in cisco site about 

Recent Comments