OpenVPN Implementation
This guide describes how to install and configure the OpenVPN Server in Linux and clients in Windows XP and Mac OSX. There are many advanced features in OpenVPN and if you’re interested in those advanced stuff, there’s a more detailed HowTo for you. This guide was created from my successful installation, so it works for me. If you find any problems or have suggestions please leave a comment. I’ll try my best to help. I’m sure, you know that you’re using this at your own risk 😉
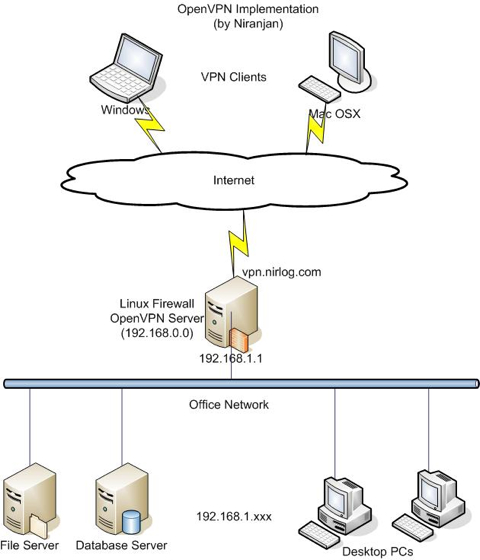
In our scenario, a small office network is protected by Linux firewall and we’ll implement the secure OpenVPN to access the internal office network (File Server, Database Server and Desktop PCs) securely from anywhere in the Internet.
OpenVPN Server Installation
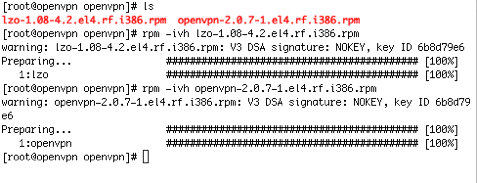
Download the OpenVPN and LZO packages, these are packaged RPMs for Fedora/Redhat, which also works for CentOS and Whiteboxlinux.
Install the packages:
Enable packet forwarding between 2 interfaces in OpenVPN Server:
#echo 1 > /proc/sys/net/ipv4/ip_forward
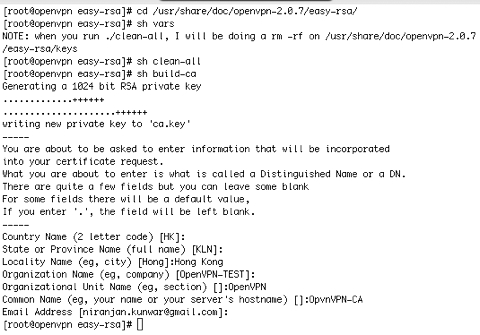
Master Certificate Authority (CA) Certificate and Key:
A set of scripts bundled with OpenVPN make the PKI management easier. We’ll use these scripts to generate a master CA certificate/key, a server certificate/key and 2 keys/certificates for separate clients.
Change your directory to easy-rsa subdirectory in your OpenVPN installation:
# cd /usr/share/doc/openvpn-2.0.7/easy-rsa
Edit the vars file and set the KEY_COUNTRY, KEY_PROVINCE, KEY_CITY, KEY_ORG, and KEY_EMAIL parameters. My vars parameters are as following, you need to setup your own:
export KEY_COUNTRY=HK
export KEY_PROVINCE=KLN
export KEY_CITY=Hong Kong
export KEY_ORG=”OpenVPN-TEST”
export KEY_EMAIL=”niranjan.kunwar@gmail.com”
Initialize the PKI:
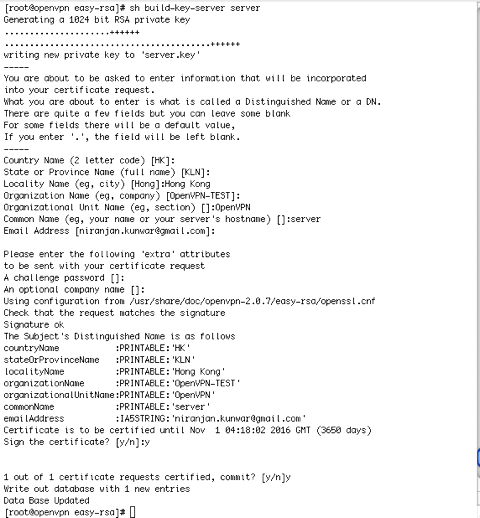
Generate Certificate and Key for the Server:
Generate Certificates and Keys for 2 clients:
#sh build-key client-win
#sh build-key client-osx
Generate Diffie Hellman parameters
Copy the keys and certificate to /etc/openvpn
#cp dh1024.pem server.crt server.key ca.crt /etc/openvpn/
Server Configuration file
A sample configuration file server.conf can be found in /usr/share/doc/openvpn-2.0.7/sample-config-files, copy it to /etc/openvpn and customize it according to your needs. There are many possible customizations that you can do to the configuration file. In our case the VPN Server will be listening to UDP port 1194, which is the official OpenVPN port number. We’ll offer the virtual address 192.168.0.0/24 to the vpn clients and push the route 192.168.1.0, which is our Office LAN subnet. Following is the contents of our configuration file server.conf:
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh1024.pem
server 192.168.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push “route 192.168.1.0 255.255.255.0”
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
Start the OpenVpn Server:
# service openvpn start
Windows Client Installation and Configuration
Download the OpenVPN GUI for Windows and install it.
Copy the ca.crt, client-win.crt and client-win.key files from OpenVPN Server to the windows pc at C:\Program Files\OpenVPN\config. A Sample client configuration file client.ovpn can be found in C:\Program Files\OpenVPN\sample-config directory, also copy it to C:\Program Files\OpenVPN\config and customize it according to your needs. Following is the contents of our client configuration file client.ovpn:
client
dev tun
proto udp
remote vpn.nirlog.com 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client-win.crt
key client-win.key
ns-cert-type server
comp-lzo
verb 3
Connect:
Ping test:
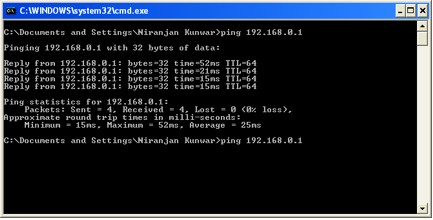
Successful ping to 192.168.0.1 shows that you can reach the server via vpn tunnel. You should be able to ping the Desktops and Servers (192.168.1.x) in the office network too.
OS X Client Installation and Configuration:
Download Tunnelblick and install it by unzipping and dragging the Tunnelblick.app to Applications folder.
Copy the ca.crt, client-osx.crt and client-osx.key files from OpenVPN Server to the Mac at /Users/<yourname>/Library/openvpn. The client configuration file openvpn.conf can be found in /Users/<yourname>/Library/openvpn directory, customize it according to your needs. Following is the contents of our client configuration file openvpn.conf:
client
dev tun
proto udp
remote vpn.nirlog.com 1194
resolv-retry infinite
nobind
user nobody
group nobody
persist-key
persist-tun
ca ca.crt
cert client-osx.crt
key client-osx.key
ns-cert-type server
comp-lzo
verb 3
Connect:
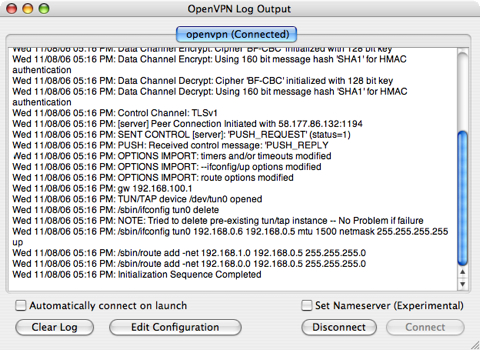
Ping test:
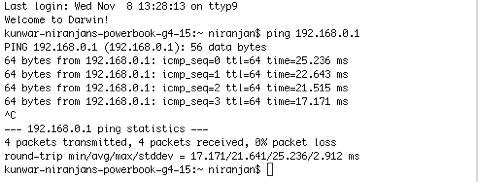
Successful ping to 192.168.0.1 shows that you can reach the server via vpn tunnel. You should be able to ping the Desktops and Servers (192.168.1.xxx) in the office network too.





The version of tunnel blick you demonstrate I was not able to get to work on Intel based macs. I had to used Tunnel blick 2.0 and I had to download separate tun/tap drivers to support the Intel based mac.
I’m using the Release Candidate 3 of Tunnelblick 3.0, which is the first Universal Binary of this application. But I’ve tested it only in PowerBook G4. I hope the final version of 3.0 will work well with Intel Macs.
Hi,
My firewall have got 2 lan card:
LAN1: 192.168.1.105/255.255.255.0 –connect to modem ADSL (192.168.1.1/255.255.255.0)
LAN2: 10.0.0.5/255.0.0.0 –connect to private LAN.
(INTERNET)
|
|
(FIREWALL)
LAN1: 192.168.1.105/255.255.255.0
|
|
LAN2: 10.0.0.5/255.0.0.0
|
|
——————–
| | |
| FTP Server WEB server
| (10.0.5.98/ (10.0.5.97/255.0.0.0)
| 255.0.0.0)
|
DB Server
(10.0.5.99/255.0.0.0)
So How can i config server.conf file ?
Hi asteriskese, you can use similar server.conf as in my example all you need to do is replace the “server” and “push route” to your LAN2 ip segment i.e. 10.0.0.0 255.0.0.0.
Hi,
thanks for your tutorial. I’ve exactly followed it but I can not ping from my windows client, the servers of my local Network (“ping 192.168.1.2” from the client is not working). I can successfully ping the VPN server (192.168.1.1 for example). What’s wrong ?
Ragards.
Hi Samba,
It might be the firewall setting in your VPN server.
Nice tutorial. Thanks for sharing