DNS Amplification Attack
Recently a new type of DNS attack have been discovered. Attackers are exploiting the recursive name servers to amplify the DDoS attacks by utilizing IP spoofing. If you want to know the very details of how this attack works then you must read DNS Amplification Attacks (pdf) by Randal Vaughn and Gadi Evron where they analyze 3 real attacks. Also this Cnet news article have some details about the attack.
At the heart of this attack is the recursive function of DNS servers. This is a very serious threat because The Measurement Factory in recent survey found that:
There are an estimated 7.5 million external DNS servers on the public Internet. Over 75% of domain name servers (of roughly 1.3 million sampled) allow recursive name service to arbitrary queriers. This opens a name server to both cache poisoning and attacks.
Here I’ve drawn the diagrams to explain what is Recursive DNS Query and how DNS Amplification Attacks work.
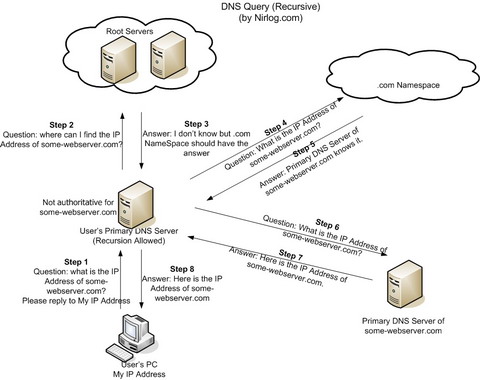
Normal DNS query (Recursive)
Step 1: The User’s PC with ip address "My IP Address" makes a DNS query to the Primary DNS Server configured in it’s TCP/IP properties, asking to resolve the ip address for some-webserver.com.
Step 2 to Step 7 (Recursive Query): User’s Primary DNS Server is not authoritative for the domain some-webserver.com. So, it asks the Root Servers which then points it to .com Namespace from where it learns about the Primary DNS Server of some-webserver.com, which replies with the IP Address of some-webserver.com.
Step 8: The IP Address of some-webserver.com is cached in the User’s Primary DNS Server and it replies to the User’s PC with the IP Address for some-webserver.com.
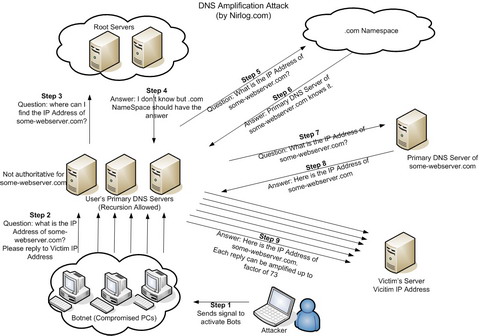
DNS Amplification Attack
Step 1: The attacker sends a signal to the compromised PCs to start DNS queries.
Step 2: All compromised PCs with spoofed ip address "Victim IP Address" make a DNS query to the Primary DNS Servers configured in their TCP/IP properties, asking to resolve the ip address for some-webserver.com.
Step 3 to Step 8 (Recursive Query): User’s Primary DNS Servers are not authoritative for the domain some-webserver.com. So, they ask the Root Servers which then points them to .com Namespace from where they learn about the Primary DNS Server of some-webserver.com, which replies with the IP Address of some-webserver.com.
Step 9: The IP Address of some-webserver.com is cached in the User’s Primary DNS Servers and they reply to the Victim’s Server (Victim IP Address) with the IP Address for some-webserver.com. The reply goes to Victim’s Server because the attacker has used this Spoofed Source IP address. The matter is made worse because this reply can be amplified up to factor of 73.
This is how the DNS amplification occurs according to DNS Amplification Attacks:
DNS amplification occurs due to the response packet being significantly larger than that of the query. If an Open Resolver receives an EDNS (RFC 2671) query containing a large buffer advertisement, its reply to the possibly-spoofed requesting IP address can be quite large. A DNS query consisting of a 60 byte request can be answered with responses of over 4000 bytes amplifying the response packet by a factor of 60.
If, for example, the response consists of a 122 byte A type response, a 4000 byte TXT response, and a 222 byte SOA response, the total response consists of 4320 bytes. This yields an amplification factor of 73
Solution:
1. Disable the Recursive functionality of DNS Servers or limit it to the clients in your network.
2. Separate the DNS Servers that are authoritative to some domains and the ones used by internal users to resolve the names.
3. Implement some sort of spoofing counter-measures such as those suggested in BCP 38






Great graphics!
Awesome article Niranjan, and I agree with purpleslog, very nice diagrams! You made it really easy to understand how the attack works.
its gud………
It maybe too late to comment… but aren’t steps 2-7 of normal query in fact an iterative query by the users dns server? The request from the user himself is indeed recursive, but “Step 2 to Step 7 (Recursive Query): ” might be a bit confusing, isn’t it?
very very very nice article
Hi there to every one, it’s truly a fastidios for me to pay a quick visit this web site, it contains helpful Information.
Thanks for any other informative website. The place
else could I am getting that type of information written in such an ideal approach?
I’ve a project that I am just now operating on, and I’ve been at the look out for such information.
Hi, of course this post is actually nice and I have learned lot of things from it regarding
blogging. thanks.
Thanks for any other fantastic article. Where else could anybody get that
type of info in such a perfect manner of writing?
I have a presentation next week, annd I’m on the look for such information.
I am genuinely grateful to the owner of this web
page who has shared this great post at at this time.
Thank you for helping us with DNS application and problems which e simple people don’t understand, Knowledge is good to have and it helps you in interview.